OTHERS INTERESTING LINKS:
- Compilation of +440 Craig Wright´s Post, Papers & Books
- Craig S. Wright academic (1988-2012)
- Grand Dad, Captain R. A. Lynam. By LISA N EDWARDS
- DEPOSITION OF DONALD JOSEPH LYNAM
-
TELEGRAMS CHANNELS: (Names in alphabetical order)
- Theory of Bitcoin – A serie from – Dr. Craig S. Wright & Ryan Charles
Academic Degrees & Professional Certifications
https://t.me/CSW_Academic @BSVGlobal Bitcoin Satoshi Vision (Craig academy) Dr. Craig Wright – A Wheelbarrow of Academic Degrees & Certificates nChain. Publicado el 30 nov. 2017 – 4 minutos
– Craig-Wright-Academic-Degrees-Certificates_2017
1988 (18 years old)

1991 (21 Years old)
01/03/1991 BUSINESS Executive Chef C&C Catering. – Nov 1994 (3 years 9 months) 
1994
5/04/1994 “…if the cash system used by you and your bank is such that all money is in-herently traceable, it will be a lot harder to commit robbery, extortion, kidnapping, and all those other horrors which people fear will come with digital cash”. Hal Finney
1996 (26 Years old)
16/09/1996 IDEOLOGY Craig Wright is on the cypherpunk mailing lists arguing in favor of capitalism To: Timothy C. May 16/09/1996 Political Risk v. Charity (was: RE: Workers Paradise. /Political rant
1997 (27 Years old)
01/04/1997 BUSINESS Information Security Australian Stock Exchange ASEApril 1997 – May 1998 (1 year 2 months) Tamaño de ASX 501-1000 empleados

01/11/1997 BUSINESS Managing Director, MD, CTO, CIO and founder. DeMorgan November 1997 – August 2003 (5 years 10 months)

1998 (28 Years old)
16/09/1998 EDUCATION Doctor of Theology, Comparitive Religous and Classical Studies 1998 – 2003
1999 (29 Years old)
2000 (30 Years old)
June 2000 Security in AUSTRALIA Version 1.0 by A. Ashbury and Craig S Wright
2001 (31 Years old)
01/02/2001 NT Security: Step-by-Step (Version 3.03) 49 pages Ridges Estate. February 2001 – September 2004 (3 years 8 months)
2003 (33 Years old)

 24/07/2003- All Dave Kleiman posts on The Cryptography Mailing List . Authors Craig & Kleiman met online: they visited the same cryptography forums and had interacted since 2003. The Satoshi Affair. Page 16 Dave Kleiman
24/07/2003- All Dave Kleiman posts on The Cryptography Mailing List . Authors Craig & Kleiman met online: they visited the same cryptography forums and had interacted since 2003. The Satoshi Affair. Page 16 Dave Kleiman
30/09/2003 BOOK by Peter Wayner. Policing Online Games – Craig cited the book explaining why “blockchain” based digital money wasn’t Bitcoin’s innovation. 2003 Dr Craig Steven Wright’s first PhD is in theology: comparative religious and classical studies, achieved in 2003 with a dissertation titled “Gnarled roots of a creation theory”.
2004 (34 Years old)
01/10/2004 BUSINESS Associate Director (Risk Services) BDO October 2004 – January 2009 (4 years 4 months) BDO
2005 (35 Years old)

 03/04/2005 QUALIFICATION: Certified Since: April 2005 Retired Certifications: GSE
03/04/2005 QUALIFICATION: Certified Since: April 2005 Retired Certifications: GSE

 25/04/2005 Implementing an Information Security Management System (ISMS) Training process. G2700 GIAC Gold Papers: 100 Pag.
25/04/2005 Implementing an Information Security Management System (ISMS) Training process. G2700 GIAC Gold Papers: 100 Pag. 
 03/09/2005 Implementing an Information Security Management System (ISMS) Global Information Assurance Certification Paper Paper. 60 Pag.
03/09/2005 Implementing an Information Security Management System (ISMS) Global Information Assurance Certification Paper Paper. 60 Pag.  16/09/2005 QUALIFICATION: Master of Statistics (MSTAT), Quantitative Statistics. University of Newcastle 2005 – 2009
16/09/2005 QUALIFICATION: Master of Statistics (MSTAT), Quantitative Statistics. University of Newcastle 2005 – 2009 


2006 (36 Years old) (8 Articles & Papers)
2006 Analysis of a Serial Based Digital Voice Recorder. 60 Pag. 09/01/2006 Electronic Contracting, New Wine in Old Bottles. SSRN
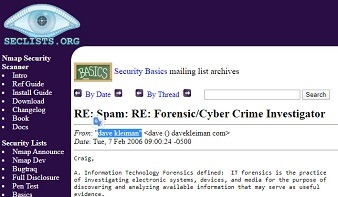
 7/02/2006 Email Forensic/Cyber Crime Investigator From: “dave kleiman To: Craig 08/02/2006 Forensic/Cyber Crime Investigator. “The facts and only the facts”. 13/02/2006 Was Forensic/Cyber Crime Investigator – Now Statistical Analysis of Digital Forensic Sciences. BDO 22/02/2006 Vulnerabilites in new laws on computer hacking. BDO
7/02/2006 Email Forensic/Cyber Crime Investigator From: “dave kleiman To: Craig 08/02/2006 Forensic/Cyber Crime Investigator. “The facts and only the facts”. 13/02/2006 Was Forensic/Cyber Crime Investigator – Now Statistical Analysis of Digital Forensic Sciences. BDO 22/02/2006 Vulnerabilites in new laws on computer hacking. BDO  22/03/2006 Email Signing before Encryption and Signing after Encryption. BDO 31/03/2006 Extending Control, API Hooking. Hakin9
22/03/2006 Email Signing before Encryption and Signing after Encryption. BDO 31/03/2006 Extending Control, API Hooking. Hakin9 

(Charles Sturt University) student number 11293457


 16/09/2006 QUALIFICATION: LLM, Law (International Commercial Law). Northumbria University 2006 – 8
16/09/2006 QUALIFICATION: LLM, Law (International Commercial Law). Northumbria University 2006 – 8  01/10/2006 A QUANTITATIVE TIME SERIES ANALYSIS OF MALWARE AND VULNERABILITY TRENDS. BDO
01/10/2006 A QUANTITATIVE TIME SERIES ANALYSIS OF MALWARE AND VULNERABILITY TRENDS. BDO 
2007 (37 Years old) (9 Articles & Papers)
1- Bitcoin: A Peer-to-Peer Electronic Cash System 8/01/2007 BOOK Complex Social Networks . Fernando Vega Redondo. Professor Universidad de Alicante 1990 – 2007 – Craig confirms Bitcoin is a small-world network. 01/01/2007 BUSINESS Mentor and Stay Sharp Instructor SANS Institute. 2015 (8 years) 01/01/2007 QUALIFICATION: Technical Director. GIAC Ethics Board until (2011) 01/01/2007 BOOK Dave Kleiman Rootkits for Dummies (For Dummies (Computer/Tech) 01/01/2007 Beyond automated tools and Frameworks – the shellcode injection process. Hakin9 03/03/2007 The Psychology of Security Dr Craig Wright • Schneier on Security 31/03/2007 Taking control, Functions to DLL injection. Hakin9 03/07/2017 Overwriting Hard Drive Data: The Great Wiping Controversy. Kleiman 14/04/2007 Concepts: Security and Obscurity. BDO 


 16/07/2007 A Taxonomy of InformationSystems Audits, Assessmentsand Reviews. . SANS Institute
16/07/2007 A Taxonomy of InformationSystems Audits, Assessmentsand Reviews. . SANS Institute  01/08/2007 The Problem With Document Destruction. Vol 10. The IIA, USA 16/09/2007 EDUCATION Psychology, Psychology. Charles Sturt University – 2010
01/08/2007 The Problem With Document Destruction. Vol 10. The IIA, USA 16/09/2007 EDUCATION Psychology, Psychology. Charles Sturt University – 2010 

 04/10/2007 . java source code audit. BDO 30/10/2007 . PAYMENTS PROVIDERS AND INTERMEDIARIES AS DEFINED IN THE LAW OF THE INTERNET.
04/10/2007 . java source code audit. BDO 30/10/2007 . PAYMENTS PROVIDERS AND INTERMEDIARIES AS DEFINED IN THE LAW OF THE INTERNET.  07/11/2007 BOOK Dave Kleiman – The Official CHFI Study Guide
07/11/2007 BOOK Dave Kleiman – The Official CHFI Study Guide 
 01/12/2007 RELIGION The Uniting Church (NSW) Trust Association Limited. United Financial Services Trustee. December 2007 – Present (2015)
01/12/2007 RELIGION The Uniting Church (NSW) Trust Association Limited. United Financial Services Trustee. December 2007 – Present (2015) 
2008 (38 Years old) (17 Articles & Papers)
 14/01/2008 ELECTRONIC CONTRACTING IN AN INSECURE WORLD
14/01/2008 ELECTRONIC CONTRACTING IN AN INSECURE WORLD 
 21/01/2008 Requirements for Record Keeping and Document Destruction in a Digital World SANS RR Oct 2007. 84 Pages
21/01/2008 Requirements for Record Keeping and Document Destruction in a Digital World SANS RR Oct 2007. 84 Pages  31/01/2008 The postal acceptance rule 01/02/2008 “Electronic Contracting in an Insecure World” SANS RR Nov 2007. 27/02/2008 ISO 27001 mapping to PCI 05/03/2008 Defamation and the diffculties of law on the Internet. This post goes to those cowards who sit behind anonymity on the web 12/03/2008 Defamation and the diffculties of law on the Internet. SANS had “Police Decline to Intervene in Libellous Bebo Page Case (March 7 & 8, 2008” in Newsbytes Vol 10. 10/04/2008 INTERVIEW Craig Wright, Security Hero – GIAC Technical Director
31/01/2008 The postal acceptance rule 01/02/2008 “Electronic Contracting in an Insecure World” SANS RR Nov 2007. 27/02/2008 ISO 27001 mapping to PCI 05/03/2008 Defamation and the diffculties of law on the Internet. This post goes to those cowards who sit behind anonymity on the web 12/03/2008 Defamation and the diffculties of law on the Internet. SANS had “Police Decline to Intervene in Libellous Bebo Page Case (March 7 & 8, 2008” in Newsbytes Vol 10. 10/04/2008 INTERVIEW Craig Wright, Security Hero – GIAC Technical Director

17/04/2008 The Impact of Internet Intermediary Liability. 90 Pages 19/04/2008 . The application, scope and limits of Letters of Indemnity 21/04/2008 . UCP 500 – successful or not. 

University of Northumbria (UK). Student Number: 05024288

 22/06/2008 DETECTING HYDANSTATISTICAL METHODS FOR CLASSIFYING THE USE OF HYDANBASED STEGONOGRAPHY IN EXECUTABLE FILES
22/06/2008 DETECTING HYDANSTATISTICAL METHODS FOR CLASSIFYING THE USE OF HYDANBASED STEGONOGRAPHY IN EXECUTABLE FILES  03/07/2008 Detecting Hydan: Statistical Methods For Classifying The Use Of Hydan Based Stegonagraphy In Executable Files. 04/07/2008 BOOK – “The IT Regulatory and Standards Compliance Handbook: How to Survive Information Systems Audit and Assessments“ 07/07/2008 Statistical Methods to Determine the Authenticity of Data.
03/07/2008 Detecting Hydan: Statistical Methods For Classifying The Use Of Hydan Based Stegonagraphy In Executable Files. 04/07/2008 BOOK – “The IT Regulatory and Standards Compliance Handbook: How to Survive Information Systems Audit and Assessments“ 07/07/2008 Statistical Methods to Determine the Authenticity of Data. 
 15/10/2008 . Wiping a drive: /dev/zero or /dev/urandom better? GSE-Compliance 27/10/2008 . How math can help with forensics. SANS
15/10/2008 . Wiping a drive: /dev/zero or /dev/urandom better? GSE-Compliance 27/10/2008 . How math can help with forensics. SANS
31/10/2008 Satoshi Nakamoto was the inventor of the bitcoin protocol, publishing a paper via the Cryptography Mailing List
14/11/2008 BOOK – Mobile Malware Attacks and Defense – 440 Pages
17/11/2008 Satoshi Nakamoto Bitcoin P2P e-cash paper: I believe I’ve worked through all those little details over the last year and a half while coding it,…. The Cryptography Mailing List To: James A Donald
05/12/2008 Forensic Mining. SANS  15/12/2008 . Destruction of adverse documents . SANS 17-22/12/2008 Searches and the US 4th Amendment . SANS 30/12/2008 Current Issues in DNS. – Sans Technology Inst, USA. 78 Pag December 2008 BOOK – Overwriting Hard Drive Data: The Great Wiping Controversy. 243 Pages (Dave Kleiman and Craig Pages 243–257)
15/12/2008 . Destruction of adverse documents . SANS 17-22/12/2008 Searches and the US 4th Amendment . SANS 30/12/2008 Current Issues in DNS. – Sans Technology Inst, USA. 78 Pag December 2008 BOOK – Overwriting Hard Drive Data: The Great Wiping Controversy. 243 Pages (Dave Kleiman and Craig Pages 243–257)
2009 (39 Years old) (16 Articles & Papers)
01/01/2009 BUSINESS Director Information Defense Pty Ltd January 2009 – June 2011 (2 years 6 months) 03/01/2009 The genesis block is dated to 3rd January, 2009. The first mined block occurred on 9th January.
12/01/2009 Hal Finney, who would receive the first bitcoin transaction, on block 9. 10 btc
11/02/2009 Overwriting can occur anytime, as long as it is done once after . SANS 18/02/2009 Free Windows Drive tools . SANS
23/02/2009 Starting a Drive Repair/Recovery Lab . SANS 11/03/2009 SQL, Databases and Forensics. SANS 15/03/2009 Forensics and Data Access Auditing . SANS 21/03/2009 Judge orders defendant to decrypt PGP-protected laptop – CNET News 27/03/2009 SQL Rootkits . SANS 01/04/2009 Code in a Flash . SANS  24/04/2009 Code skills make better Forensic Analysts . SANS 27/04/2009 Using HELIX LIVE for Windows . SANS 29/04/2009 System Scanner . SANS 01/05/2009 BUSINESS Vice President, Forensics Services. iVolution Security (6 years) 11/05/2009 A Step-by-Step introduction to using the AUTOPSY Forensic Browser .SANS 22/05/2009 BOOK – Official (ISC)2 Guide to the CISSP(R)-ISSMP(R) CBK “Law, Investigations, Forensics and Ethics“. 22/06/2009 Live Investigations .SANS
24/04/2009 Code skills make better Forensic Analysts . SANS 27/04/2009 Using HELIX LIVE for Windows . SANS 29/04/2009 System Scanner . SANS 01/05/2009 BUSINESS Vice President, Forensics Services. iVolution Security (6 years) 11/05/2009 A Step-by-Step introduction to using the AUTOPSY Forensic Browser .SANS 22/05/2009 BOOK – Official (ISC)2 Guide to the CISSP(R)-ISSMP(R) CBK “Law, Investigations, Forensics and Ethics“. 22/06/2009 Live Investigations .SANS 
 29/06/2009 . Hard Drive Errors and Replacements . SANS
29/06/2009 . Hard Drive Errors and Replacements . SANS  16/09/2009 EDUCATION PhD, Computer Science. Charles Sturt University – 2012
16/09/2009 EDUCATION PhD, Computer Science. Charles Sturt University – 2012  28/09/2009 . Reverse Enginnering Java . SANS 03/11/2009 An Analysis of SpyKing . SANS
28/09/2009 . Reverse Enginnering Java . SANS 03/11/2009 An Analysis of SpyKing . SANS 
2010 (40 Years old) (16 Articles & Papers)
9/02/2010 Modelling Risk. blog personal
9/02/2010 how about accepting a challenge to an open debate on the subject at Defcon?
12/02/2010 . Risk measurements. “Risk and economics matter to security.”
09/03/2010 . Building a UNIX/Linux Incident response / Forensic Disk . SANS
10/03/2010 . Unix Logging . SANS
12/03/2010 . Unix Network and System profiling . SANS
15/03/2010 . Finding out about other users on a Linux system . SANS
22/03/2010 . Finer Points of Find . SANS
24/03/2010 . Unix System Accounting and Process Accounting . SANS  09/04/2010 . Undersanding *NIX File Linking (ln) . SANS
09/04/2010 . Undersanding *NIX File Linking (ln) . SANS
13/04/2010 . An anti-forensics dd primer . SANS
28/05/2010 Criminal Specialization as a corollary of Rational Choice.” ICBIFE, HK
24/06/2010 . NDIFF for incident detection . SANS
13/07/2010 . Linux Programming Tools . SANS
24/08/2010 Packer Analysis Report – Debugging and unpacking the NsPack 3.4 and 3.7 packer. Sans Technology Inst, USA  30/11/2010 The Economics of Developing Security Embedded Software. 12 Pages Charles Sturt University
30/11/2010 The Economics of Developing Security Embedded Software. 12 Pages Charles Sturt University
01/12/2010 Software, Vendors and Reputation: an analysis of the dilemma in creating secure software” Intrust 2010 China
13/12/2010 Software, vendors and reputation: An analysis of the dilemma in creating secure software. Charles Sturt University
2010 BUSINESS Wright began working for Bodog in 2010, Ayre featured in the 2006 “billionaires” issue of Forbes magazine.
2011 (41 Years old) (23 Articles & Papers)
 2011 Rationally Opting for the Insecure Alternative: Negative Externalities and the Selection of Security Controls. CISIS Spain
2011 Rationally Opting for the Insecure Alternative: Negative Externalities and the Selection of Security Controls. CISIS Spain
08/01/2011 A Quantitative Analysis into the Economics of Correcting Software . CISIS Spain 2010  25/01/2011 . Erasing drives should be quick and easy. SANS
25/01/2011 . Erasing drives should be quick and easy. SANS
26/01/2011 Using checklists to make better best Craig S. Wright, Tanveer A. Zia 

 15/02/2011 Modeling System Audit as a Sequential test with Discovery as a Failure Time Endpoint” ICBIFE, HK. Wright, C & Via, T (2011)
15/02/2011 Modeling System Audit as a Sequential test with Discovery as a Failure Time Endpoint” ICBIFE, HK. Wright, C & Via, T (2011)
11/04/2011 BOOK Official (ISC)2® Guide to the ISSMP® CBK® ((ISC)2 Press)– 470 Pag. 11/04/2011 BUSINESS Asia Pacific Director, VP GICSR | Global Institute for Cyber Security + Research – February 2012 (11 months)

23/04/2011 Satoshi disappeared from the Bitcoin forums “I’ve moved on to other things. It’s in good hands with Gavin and everyone”. said to Mike Hearn
01/06/2011 Scanning for Malware Offline is Essential
10/06/2011 Rationally Opting for the Insecure Alternative: Negative Externalities and the Selection of Security Controls . Charles Sturt University 8 Pages
10/06/2011 A Quantitative Analysis into the Economics of Correcting Software Bugs 4th International Conference on Computational Intelligence in Security for Information Systems: CISIS 2011 – Hotel Melia Costa del Sol, Torremolinos, Málaga, Spain Chapter 4: Securing Software. Pages 198-205
20/06/2011 A comparative study of attacks against Corporate IIS and Apache Web Serv
14/07/2011 What makes an expert?  26/07/2011 Why didn’t Google catch the Norway killer?
26/07/2011 Why didn’t Google catch the Norway killer?
29/07/2011 Are Anonymous and LulzSec about to hack PayPal for WikiLeaks?
4/08/2011 World’s biggest-ever cyber attacks uncovered – and it’s only the beginning
9/08/2011 LulzSec, Anonymous … freedom fighters or the new face of evil? Craig S Wright  24/08/2011 Starting to Write Your Own Shellcode 4 Pages
24/08/2011 Starting to Write Your Own Shellcode 4 Pages
24/08/2011 A preamble into aligning Systems engineering and Information security risk measures” ICBIFE, HK 24/08/2011 Exploiting format Strings with Python. Hakin9
24/08/2011 Starting to write your own shellcode. Hakin9
31/08/2011 BOOK – Check Point NGX R65 Security Administration– 800 Pages
05/09/2011 Rationally opting for the insecure alternative: Negative externalities and the selection of security controls. 20 pag
20/09/2011 the Law Says about Distributing a Virus or Malware
26/09/2011 SCADA: Air Gaps Do Not Exist
11/10/2011 A Preamble into Aligning Systems Engineering and Information Security Risk 38 Pages 30/10/2011 BOOK – A quantitative analysis into the economics of correcting software bugs. 12 Pages (Pages 198–205)
01/11/2011 Of Black Swans, Platypii and Bunyips. The outlier and normal incident in risk management. CACS2011 Australia
01/12/2011 A comparative study of attacks against Corporate IIS and Apache Web Servers. Sans Technology Inst, USA
07/12/2011 Using checklists to make better best. Charles Sturt University
13/12/2011 Modeling system audit as a sequential test with discovery as a failure time endpoint. 2011 International Conference on Business Intelligence and Financial Engineering: ICBIFE 2011 – Hong Kong, Craig W, Tanveer Zia. Charles Sturt University
23/12/2011 BUSINESS Eventually, later in 2011, I started working on a company called Panopticrypt. The story of Bitcoin,
2012 (42 Years old)
01/01/2012 BUSINESS Executive Vice President, Strategic Development CSCSS / Centre for Strategic Cyberspace + Security Science. – July 2015 (3 years) London, UK  24/08/2012 Group Selection and Cyber Terror. 5 Pages
24/08/2012 Group Selection and Cyber Terror. 5 Pages  18/10/2012 BUSINESS Denariuz Ltd is a Private Company Limited. Doncaster, South Yorkshire. 05/12/2012 . Territorial behavior and the economics of Botnets
18/10/2012 BUSINESS Denariuz Ltd is a Private Company Limited. Doncaster, South Yorkshire. 05/12/2012 . Territorial behavior and the economics of Botnets
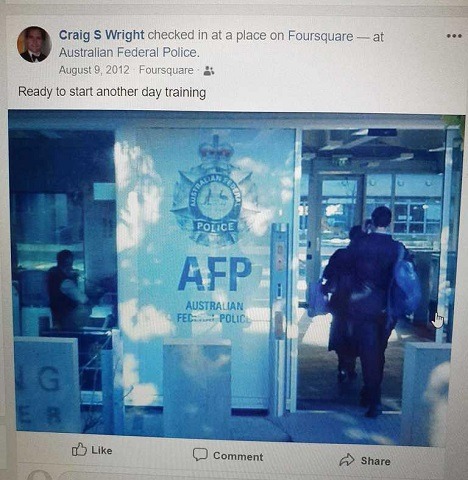
2013 (43 Years old)
2017




https://ramonquesada.com/english/compilation-craig-wright/
Compilation of +440 Craig Wright´s Post, Papers & Books in chronological order (Open list) (0 submissions)

Craig S. Wright academic (1992-2012)
https://ramonquesada.com/english/craig-s-wright-academic/
SATOSHI´S CLOSE CONTACTS:
- If I’d Known What We Were Starting. By Ray Dillinger.
- Interview with Ray Dillinger
- Bitcoin and me. By Hal Finney
- Interview with Laszlo Hanyecz
CRAIG IS SATOSHI:
- I believe Craig Steven Wright is the person who invented Bitcoin. By Gavin Andresen
- SATOSHI IS DEAD – LONG LIVE SATOSHI. By Ian Grigg
- How I Met Satoshi. By Jon Matonis
- Is he Satoshi or is he my Brother? By Danni DeMorgan
- La saga Satoshi continúa: Joseph Vaughn Perling
WHO IS…?:
CRAIG´S ARTICLES:
- BTC y la censura. By Craig Wright
- Evidencia y ley By Craig Wright
- La historia de Bitcoin, continuación… (Segunda parte) By Craig Wright
- Cuidado con lo que deseas… By Craig Wright
OTHERS INTERESTING LINKS:
- Compilation of +440 Craig Wright´s Post, Papers & Books
- Craig S. Wright academic (1992-2012)
- Grand Dad, Captain R. A. Lynam. By LISA N EDWARDS
- DEPOSITION OF DONALD JOSEPH LYNAM
- Theory of Bitcoin – A serie from – Dr. Craig S. Wright & Ryan Charles
This post was created with our nice and easy submission form. Create your post!







